Examining the Windows Pagefile.sys for Forensic Investigations
The Pagefile.sys is a virtual memory file used by the Windows OS, also commonly known as a swap file. Windows uses this file as a supplement to the physical RAM if it encounters a file or program that utilizes more than the physical RAM capacity, basically it’s substituting file space on the hard disk for actual RAM. Depending on how the victim machine is used and set up, the Pagefile can contain some valuable pieces of information for a forensic examiner. Since the Pagefile is used as a RAM substitute, it generally won't contain whole files and will most likely contain random strings of data that a program didn’t need at the time of the swap. Still, it's worth a dig since you never know what little piece of information can make or break an investigation.
The Pagefile.sys is located in the root directory of the system drive and can either be extracted from an already captured image or using tools such as FTK Imager from the target machine. Since the file basically contains memory blocks, the extraction process is just like RAM analysis. It can be run through Voluntlity, through a carver or Bulk Extractor, or even as simple as running the Strings command against it.
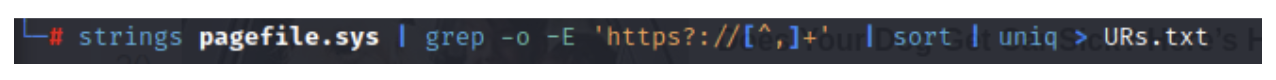
In the example below, we are going the Strings route. We just want to quickly see if there are any additional URLs in the recent usage that piqued our interest, specifically because in this instance the user is accused of inappropriate web usage, the fact that all the browsers were wiped is the first clue that there might be some truth to that. There are multiple ways to use grep for urls, so we are just going to keep it simple and look for any HTTPS sites and push that to a text file.
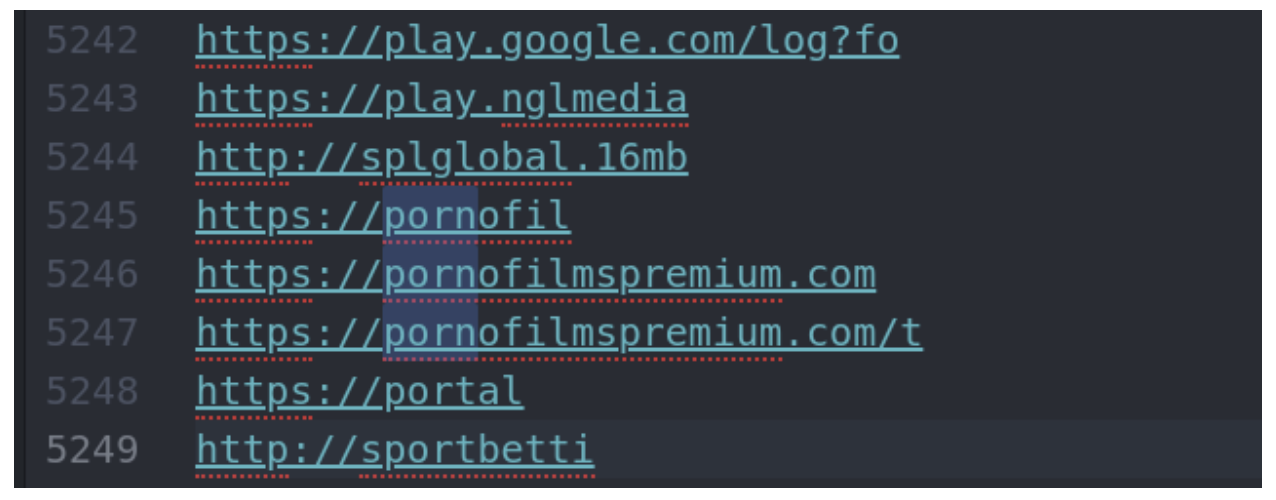
Within the results, we found a lot of useless information, but a quick browse did find some interesting URLs, as seen below. Clearly, at some point, either the user went to these sites or was on a website that contained links or ads to inappropriate sites. The beauty of grep is that you can search for anything that interests you like URLs, emails, phone numbers, or clear text passwords. So we can always run additional grep commands against the Pagefile.sys to see what else it is hiding.
So, to conclude, the Pagefile.sys is often overlooked during investigations, mostly because it doesn’t produce whole files or easily read data, but it can help fill in the gaps, especially in malware cases. At ArcPoint, we came to that conclusion early on, so we made sure ATRIO could extract both Pagefile.sys and Hiberfil.sys so that they could both be examined later to supplement the usual evidence in the investigation.