Bitlocker Detection From The Command Line
In this scenario, we’re going to look at how to tell if a partition is encrypted with Bitlocker from the linux command line. This can be important if you are using forensic tools on a linux system or need to script the detection of Bitlocker (or any really any kind of signature found on a drive).
I figured this out during an exploitation where I had to evaluate the partitions of a windows drive. My primary computer was fully utilized by another task and I ended up using an old laptop running linux to evaluate the previously acquired E01 image. When I wasn’t able to read the filesystem on the OS partition I knew I needed to figure out whether Bitlocker had been enabled or if the problem was something else entirely. So, these are the steps I took.
This process assumes the drive has previously been imaged as an E01 or raw dd. The process for doing this will be to:
Read the partition table using The Sleuth Kit’s mmls tool.
Identify the partitions we want to evaluate for encryption.
Identify the sector offset for the start of the partition as well as the offset at the point at which we want to stop the evaluation.
Read the beginning of the partition with a hex viewer.
Look for the signatures FVE-FS to identify Bitlocker
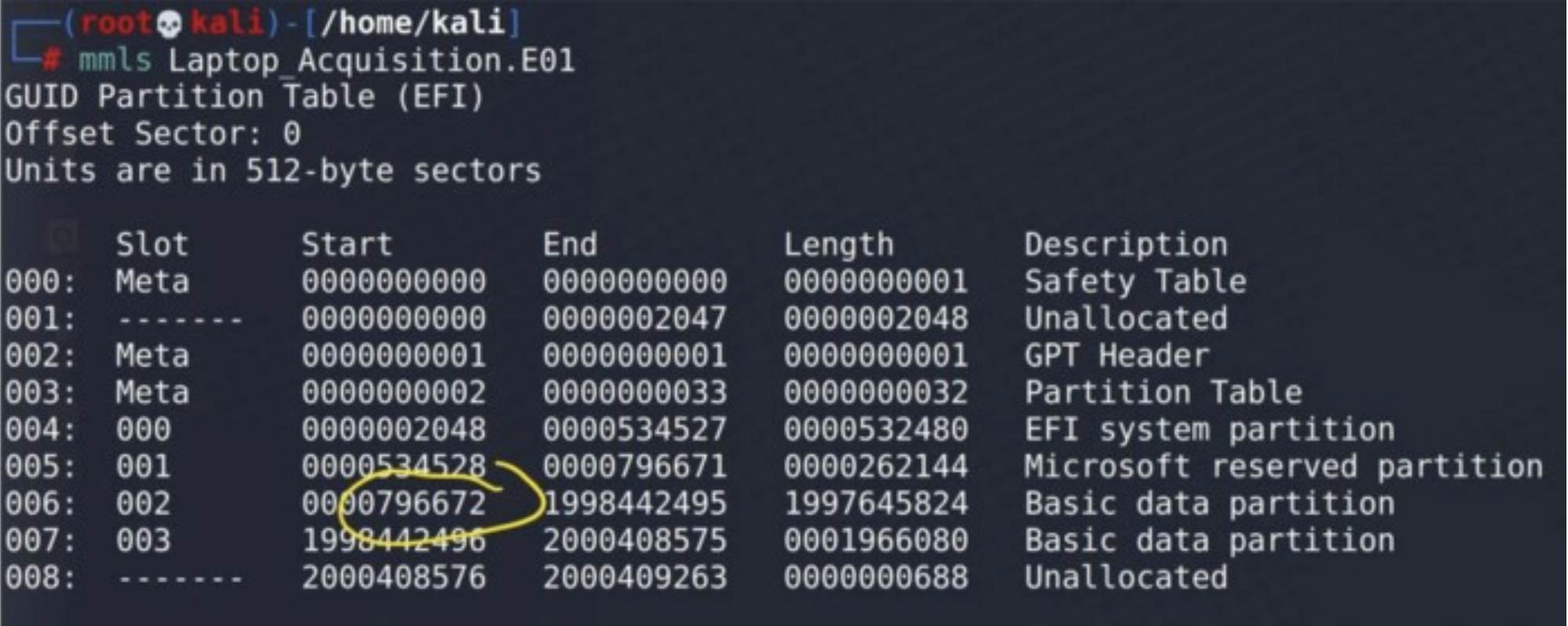
To identify a partition we might be interested in evaluating, we’re first going to run the command mmls against the E01 to read the partition table. This will provide the sector offset for the beginning and end of each partition. For our purpose, we are only interested in the starting sector offset. The partition offset that we want to evaluate for this E01 is the first partition referred to as Basic data partition, located at sector offset 796672.
IMAGE_0.jpg [MMLS output]
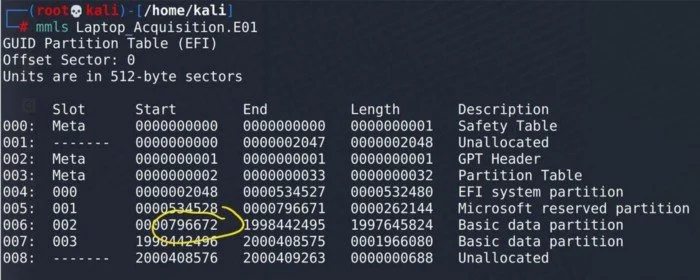
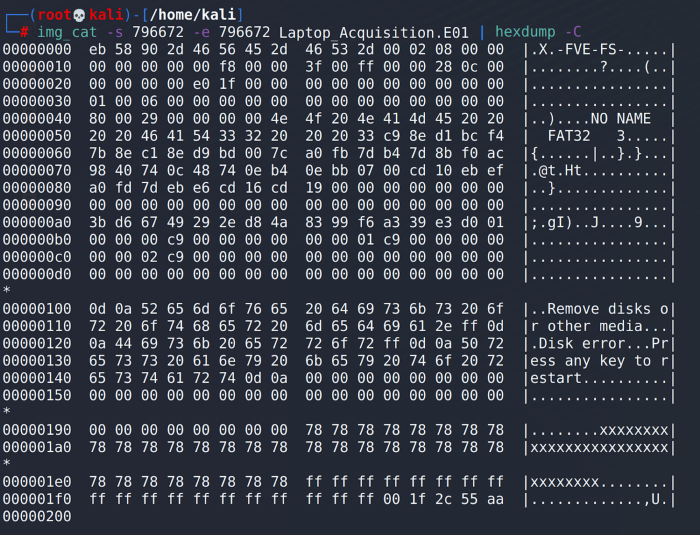
The next step will be to read the E01 at sector offset 796672. To do this we run the the tool img_cat with the -s option for the starting offset and the -eoption for the ending offset. Since the Bitlocker header resides at the very beginning of a partition, we are only interested in the first sector of data. So for our example, we will use the starting offset as both the starting and the ending offset. We will then point img_cat at the E01 to be read.
IMAGE_1.png [img_cat output]
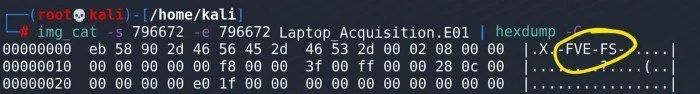
At this point we can already see the FVE-FS signature in the output, but I prefer to work with consistent and familiar output and will pipe the output from img_cat to hexdump. This allows me to confidently script and automate a search in future projects.
IMAGE_2.png [hexdump]
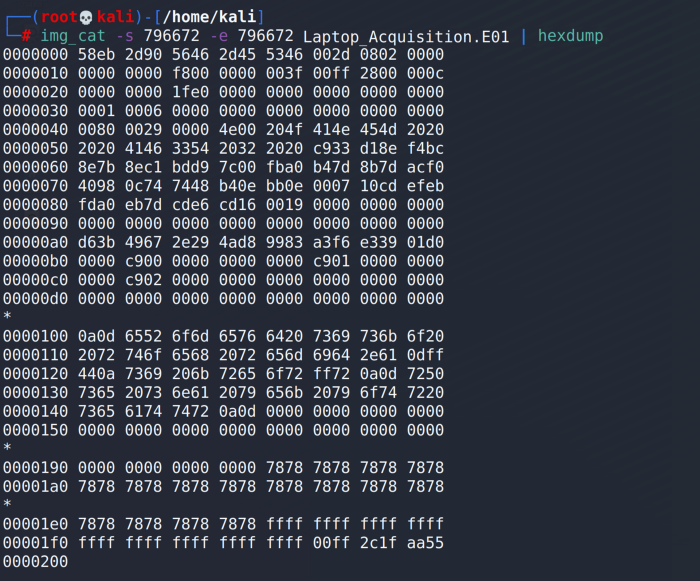
Since we’re going to search by the string (keyword) FVE-FS, we want to use the -C option with hexdump. The canonical output from the -C switch will provide both the hex as well as the ASCII representation of the data.
IMAGE_3.png [canonical hexdump]
Now that we have the output from img_cat in hex and ASCII, we can clearly see that the Bitlocker signature of FVE-FS is present at the beginning of this partition.
IMAGE_4.jpg [signature match]
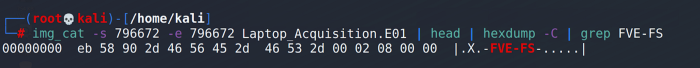
To simplify the output we’re going to add two more pipes to our line. We’re going to add the tools head before hexdump and grep for FVE-FS after the hexdump. The final line to identify bitlocker on a partition will look like this:
img_cat -s 796672 -e 796672 Laptop_Acquisition.E01 | head | hexdump -C | grep FVE-FS
IMAGE_5.png [grep match]
Now that we’ve figured out how to read the beginning of a partition for the Bitlocker header from the command line, we can test this against other partitions of interest or script an automated process for detecting Bitlocker. The good thing about this method is that we can also apply it to search for other signatures of interest.