Regripper 3.0: New Scalpel-Like Capabilities for Automated Registry Analysis
Regripper is a powerful open source registry analysis tool created by Harlan Carvey that uses plugins to extract relevant data from the individual registry hives in Windows. The tool can be used via command line in a Linux environment or within Windows using the command line or a GUI. Much has been written about the tool, so we won't go into too much detail but we do want to highlight how it can be useful and how you can modify it to create a scalpel approach against the mighty registry.
In the past, you had to tell Regripper what kind of hive file you are attempting to analyze and then tell it what profile or specific plugin you want to run. Now in Regripper 3.0, the tool can automatically distinguish what kind of hive file it is and will run all available plugins for that hive against it. In the Linux command line, this is done with the “-a” switch. In the command below we are running Regripper against the System hive and telling it to run all plugins available for that particular hive:
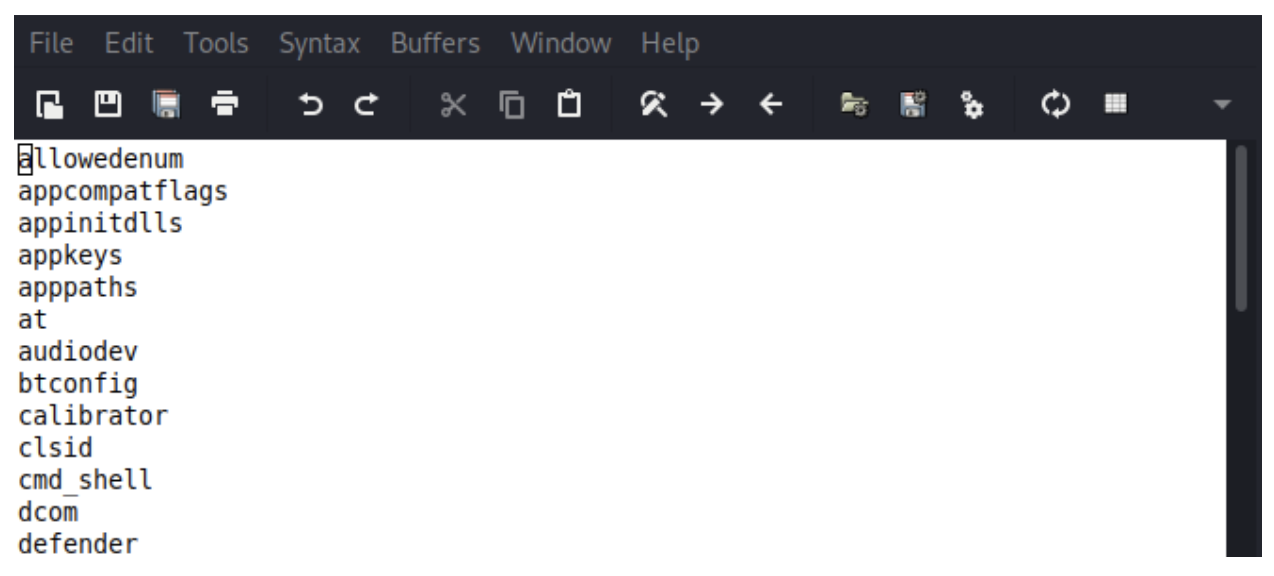
To view what plugins Regripper runs for each hive type, we have to take a look at the default profiles within the Plugins folder. In a Linux installation this folder is located in ‘/usr/lib/regripper/’. The Plugins folder contains all the individual plugins that come standard with the tool, about 250+, and the default profiles. The profiles are simply basic text files that contain a list of plugins to be run. For example, below is a snapshot of the default Software hive profile:
Now for the part that interests us, you can create your own profiles to better suit your needs instead of throwing every module against the particular hive. This can be extremely useful if you come across situations where you just need specific data from a target’s registry, for example just networking data or in our example further below just USB device data. To create your own profile, simply create a new text file within the Plugins folder and write the name of the plugins you wish to run, line by line. It should look like the example above. Once you are done, name the file something specific that you will remember and save it. It’s that easy.
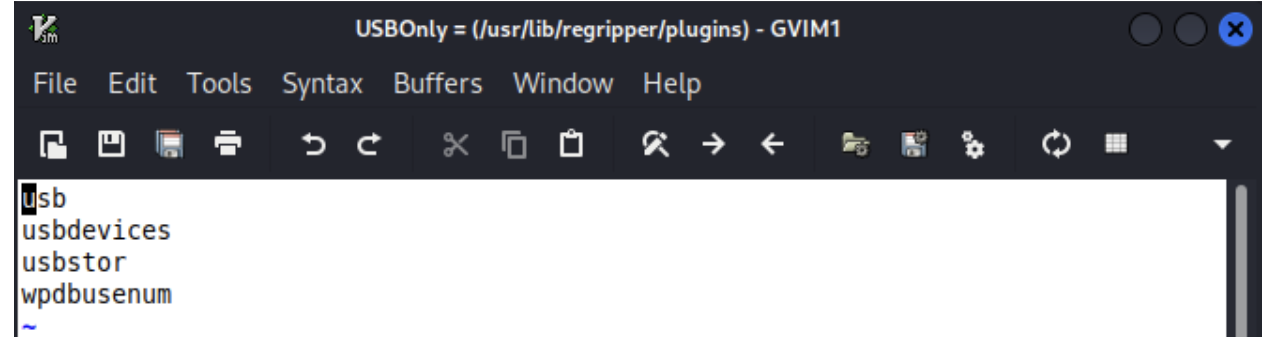
So for our example, we want to create a USB device specific profile. We get asked the same questions regarding target devices and one of them is always “What USB devices were connected to it?”. So to grab that data, we created our own USB profile and use that to quickly gather all the removable device data from the System hive. We created a new text file in the Plugins folder and named it ‘USBOnly’ and placed the four plugins we want to run:
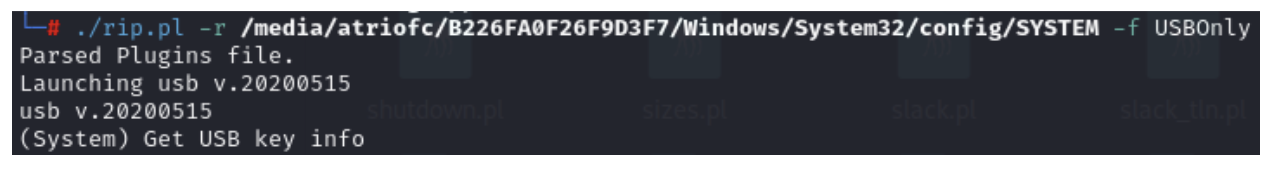
Now that we have our custom profile, we can tell Regripper to run that profile on the System hive to quickly and only grab USB device information. This can be done using the ‘-f’ switch followed by the profile name:
Regripper is a great tool to extract data from Windows registry and with the current version running it has gotten even easier. From the clean Windows GUI to the simple commands, it's a powerful tool to have in your tool box. It gets even better once you start creating your own profiles to tailor the exploitation to your cases’ needs. These custom profiles enable you to hit the registry with a scalpel and extract only the relevant data instead of looking through everything Regripper spits out at you.
Remember, ATRIO is here to help you extract the most relevant data possible for your investigations. Contact us today to learn more about our data extraction services.