Matching the Hash for Quick Wins with ATRIO
Intro
We've all been there before. We're handed a piece of evidence, and we’re asked for immediate support and a rapid turnaround of results. In this blog, we're going to highlight how ATRIO can return results quickly and efficiently to give you that quick win and identify files you know are nefarious.
One of ATRIO’s unique features is its ability to simultaneously provide real-time results while acquiring data. This dramatically reduces the time an examiner needs to spend looking for a piece of evidence they can use in their case, and ATRIO makes it a straightforward process. In this instance, we’ll look at how hash matching works to quickly identify files you already know are malicious.
Acquisition and Hash Searching
In this scenario, let’s say you’re on the scene of an investigation and you have limited time to look for the smoking gun. You suspect the person in question has connections to nefarious activities and likely contains previously identified nefarious files on their own personal devices. And because you’re prepared, you've arrived on the scene with a hash list of files you’ve already encountered that may be on the suspect’s media.
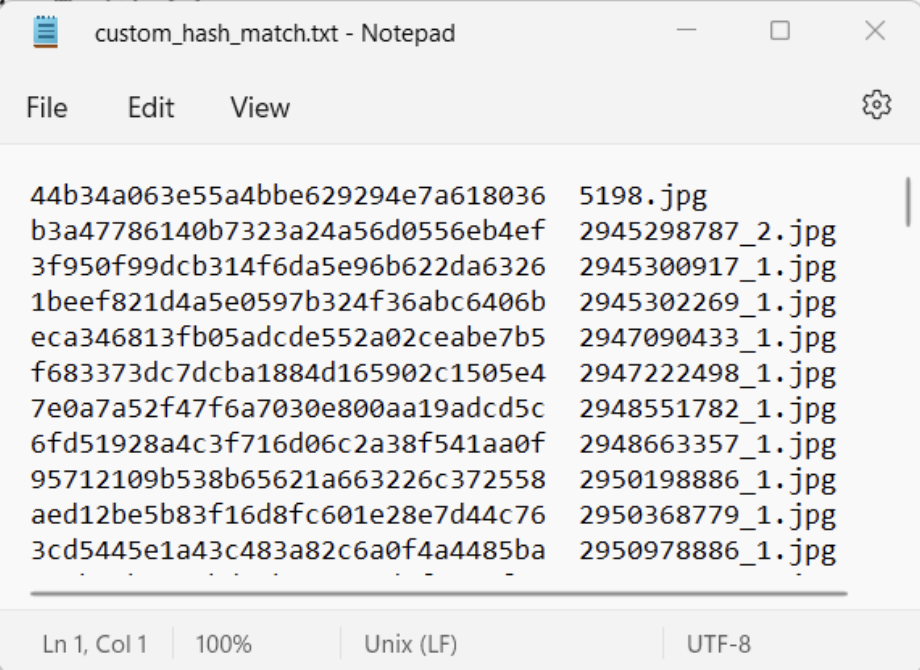
Below is an example of what you have prepared. A file named ‘custom_hash_match.txt’ on the root of your destination drive with a list of hashes and the associated file names to populate onto ATRIO.
With this hash list, ATRIO can help you quickly identify those files on the media by selecting only a few options; "hashing" and "MD5 | MATCH", as shown below.
This means that even before the drive has finished imaging, you could have hits from your hash list!
Triaging and Hash Searching
Let's say you’re back in your lab and already have an image of the suspects' drive. You don’t need another image of the suspect drive and you can use ATRIO to look at the E01 image to identify those suspected files. You insert the hash list on the root of the destination drive and select “MD5 Match” list and press GO. The only difference between the process of using a hash list while imaging a drive vs from an E01 was the selection of only one additional button!
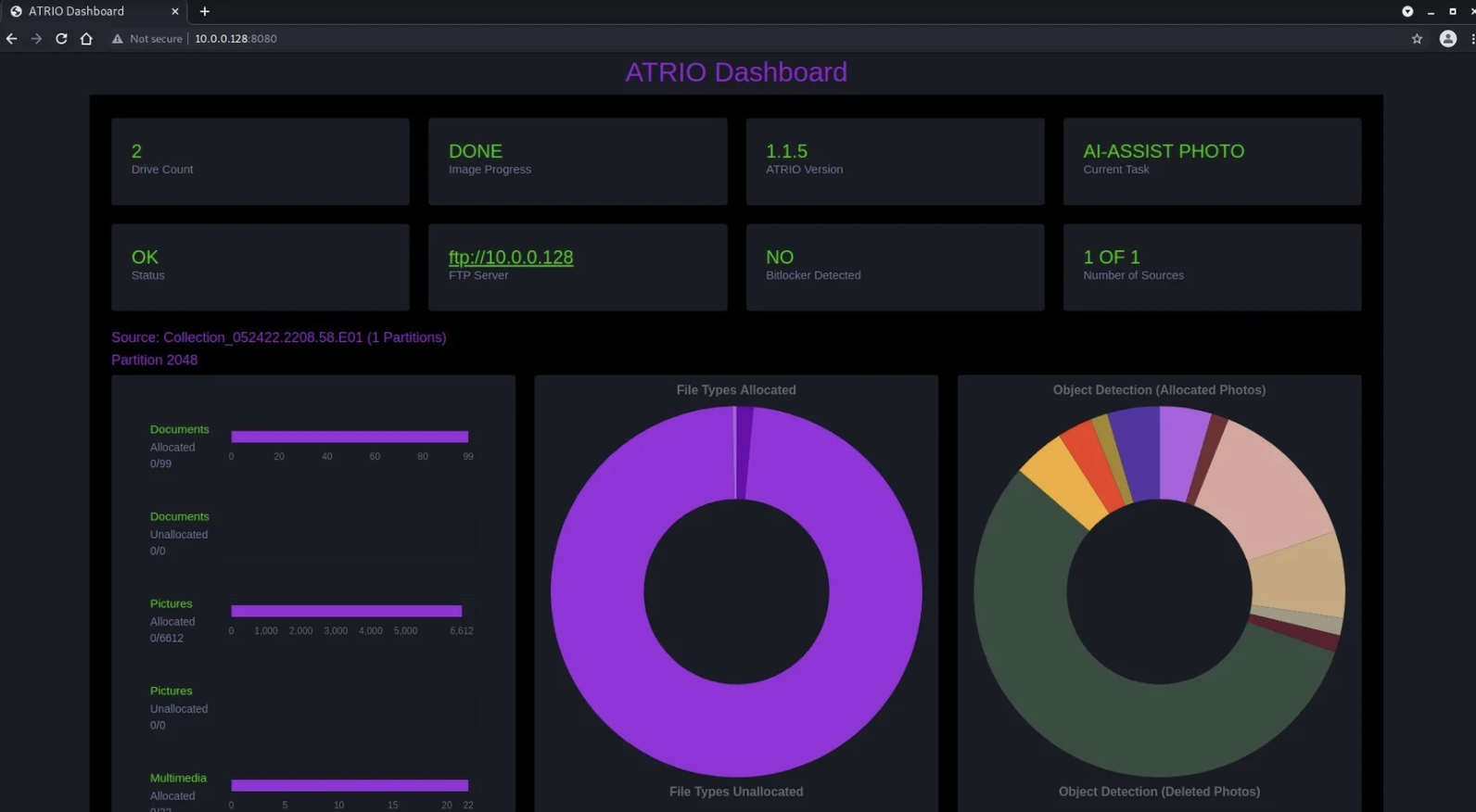
ATRIO can also show you results on the dashboard to keep you up to date with all its reports as hits happen. And you can start looking at those reports even while it’s still processing and triaging.
Conclusion
In both examples, ATRIO was able to quickly identify files based on a user-provided hash list. Having a hash list allows you to know without any doubt that two files are the same. This empowers organizations with terabytes of data to quickly have ATRIO filter through thousands of files and pick out the ones pertinent to your case.